.avif)
Key communication security challenges facing regulated organizations
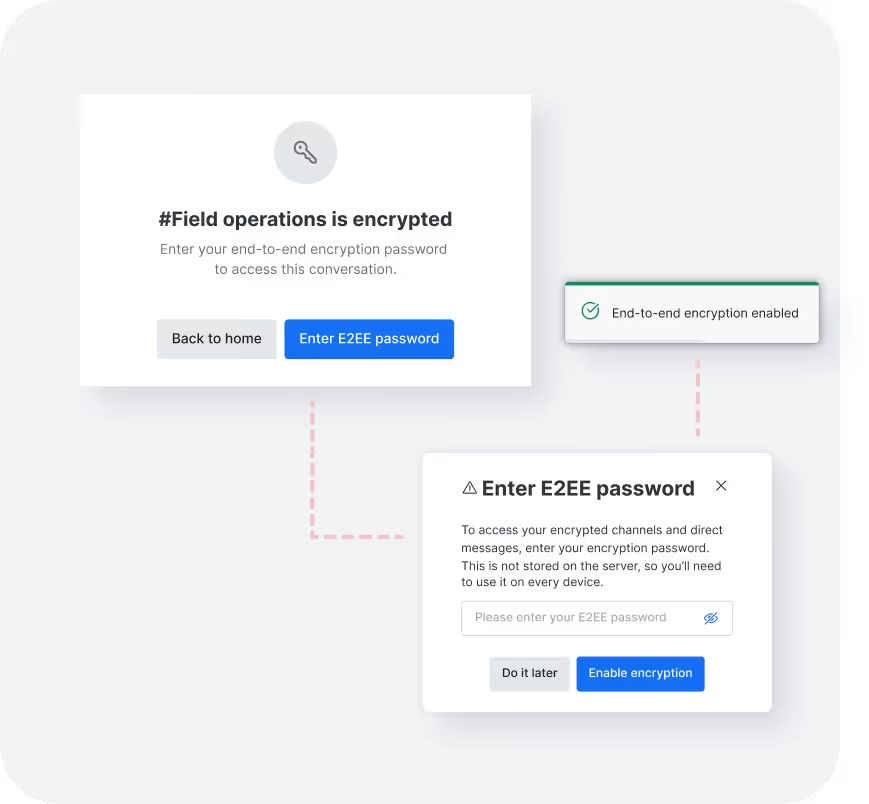
Lack of data control undermines security and compliance: Third-party cloud platforms dictate data location and access, lacking proper encryption and governance controls—making breaches harder to prevent and regulatory demands harder to meet.
Critical operations need communications that withstand network compromise: Government and critical infrastructure teams require operational continuity during cyberattacks or crises when primary networks fail.
Incompatible tools hinder collaboration with external partners: Agencies and partners on different platforms face collaboration silos, leading to inefficient workarounds or insecure alternative channels.





.png)
.png)


.avif)
.avif)
.avif)
.avif)
.avif)
.avif)

.avif)





.avif)