
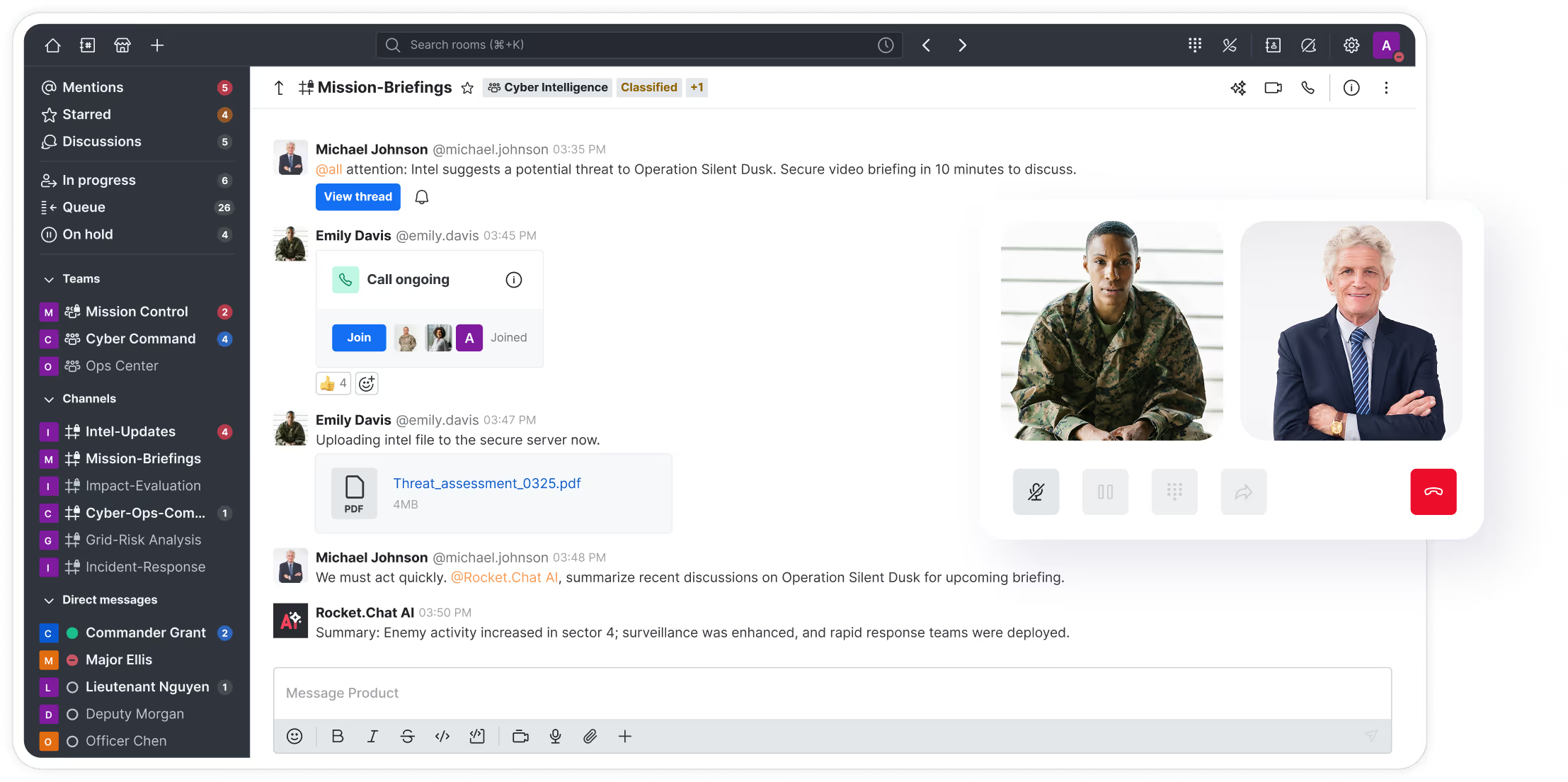
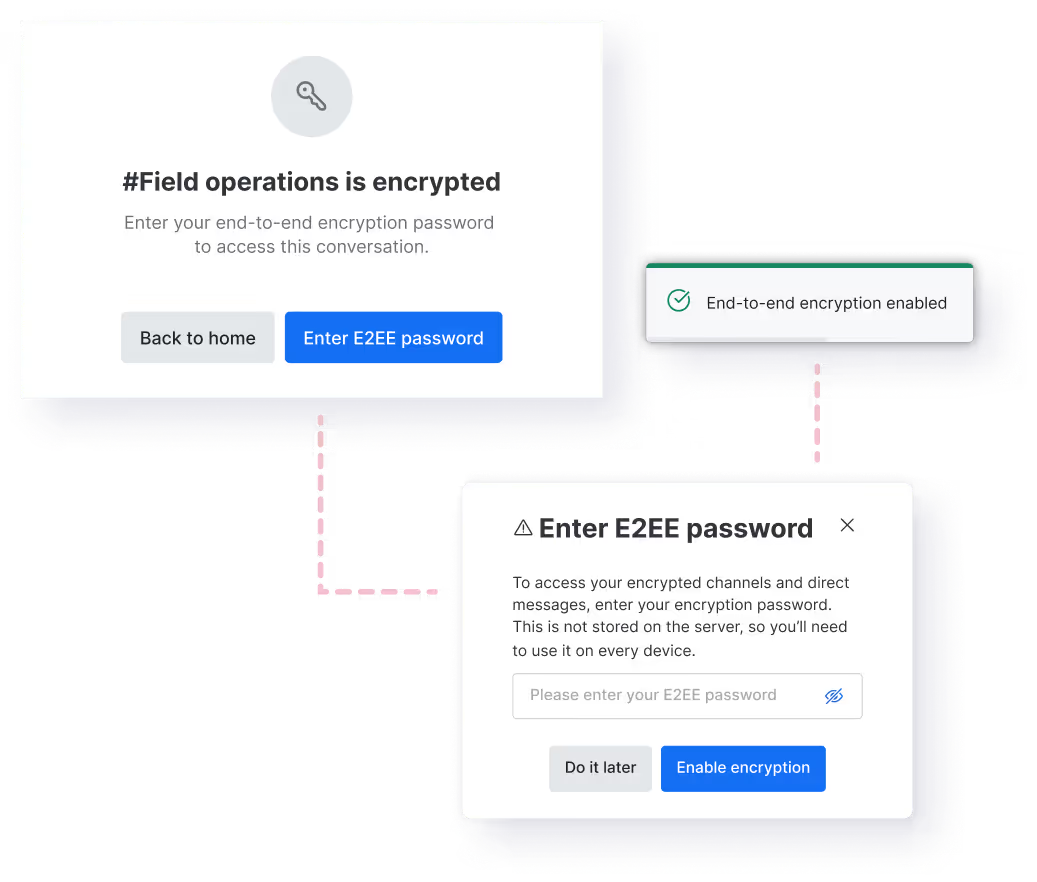
Encrypted communications for defense and military environments
Shadow IT opens doors: Unapproved tools bypass security controls and create unmonitored breach points.
Compliance slows coordination: Meeting Zero Trust and NIST standards while enabling teamwork feels impossible.
Tool sprawl breaks mission flow: Multiple disconnected systems prevent unified, secure communications across teams.





.png)
.png)

%201%20(1).avif)
.avif)

.avif)






