Ensure mission success with secure, compliant communications that enable faster decisions, safer operations,
and full control across any federal environment.







Modernizing legacy systems, eliminating shadow IT, and meeting Zero Trust and compliance mandates are non-negotiable.
of cyberattacks involve shadow IT, leading to costly breaches
of gov execs say cross-sector work boosts mission success
security incidents hit federal agencies in
2022 alone
When the mission requires absolute confidentiality, speed, and infrastructure sovereignty—Rocket.Chat delivers:
Operational agility: Accelerate secure collaboration with strict access controls.
Data control: Keep data fully within your infrastructure and control.
Compliance confidence: Aligned with federal frameworks from day one.
Procurement-ready: Flexible licensing and support for federal contracts.
Visit our Trust Center for verified security and compliance insights →







Collaborate securely, move faster, and stay compliant — all on your terms.
Powering secure, agile, and compliant federal operations
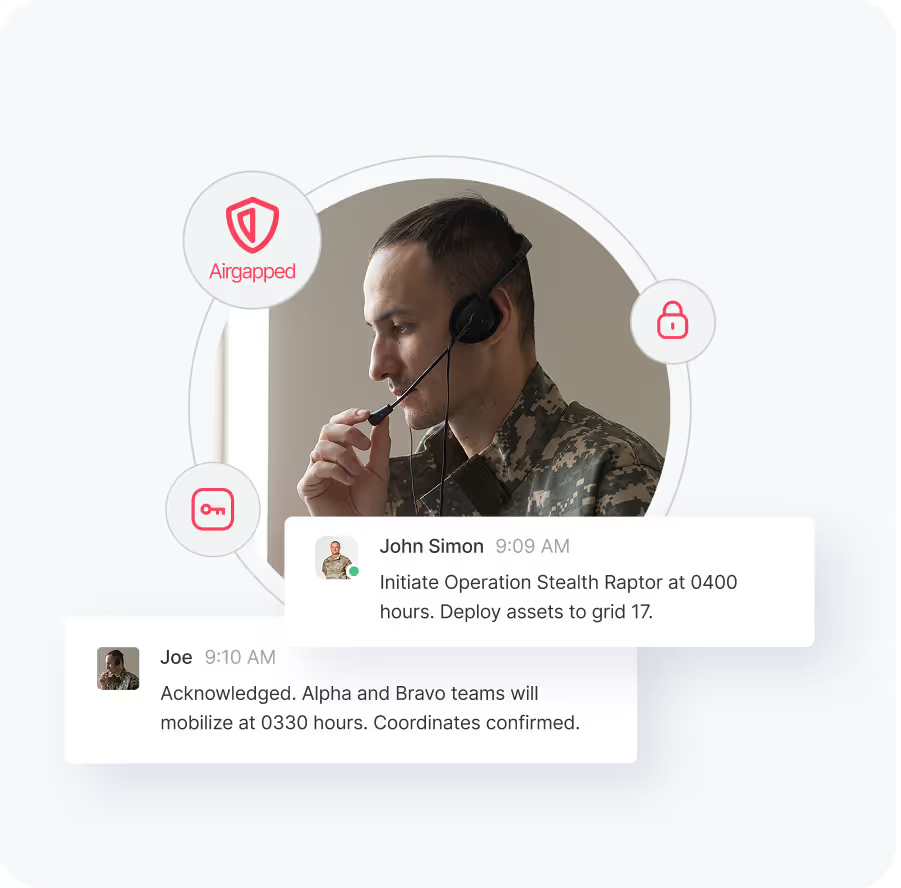
Run on-prem, in secure cloud, or fully air-gapped environments.
Restrict access by role, clearance level, or operational need.
Apply retention rules and support audits with full message traceability.
Protect data with Zero Trust architecture and end-to-end encryption.
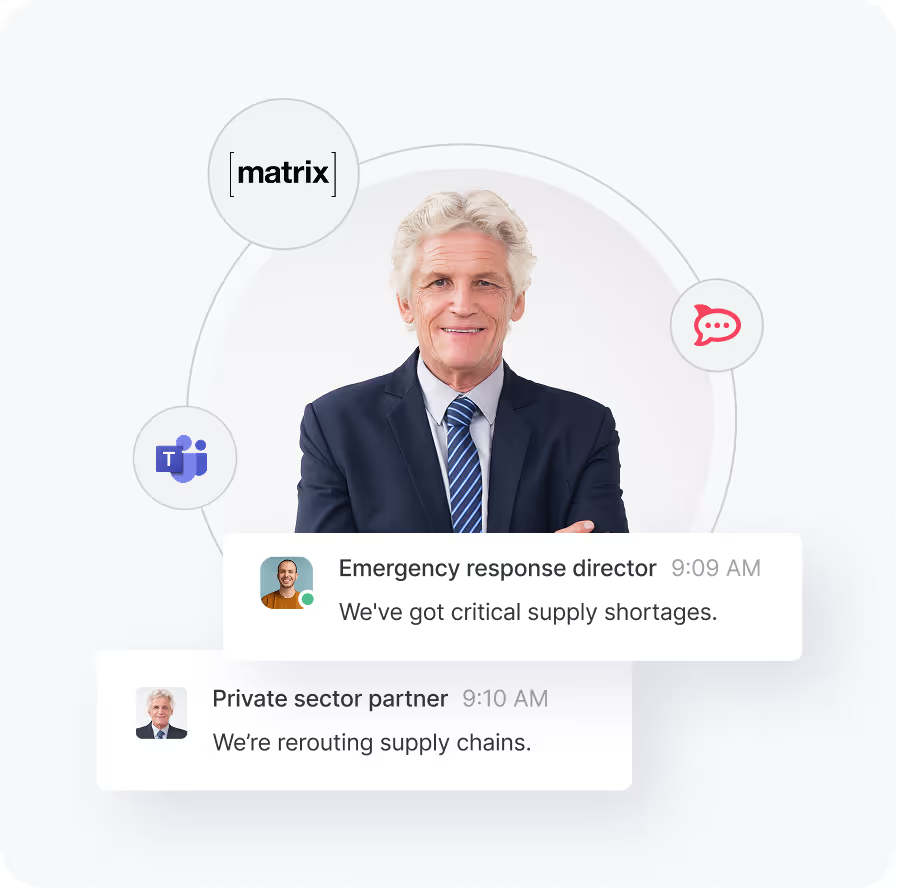
Integrate with existing tools, systems, and critical workflows.
Customize the UI and extend functionality to meet unique agency needs.
Leverage AI to streamline decision-making, enhance operational tempo, and maintain full control over sensitive information.




Supports U.S. federal agencies and critical infrastructure operators in aligning with NIST 800-53, 800-171, and Zero Trust guidance for secure, resilient, and compliant communication environments.
Encrypt data and control access across all communication
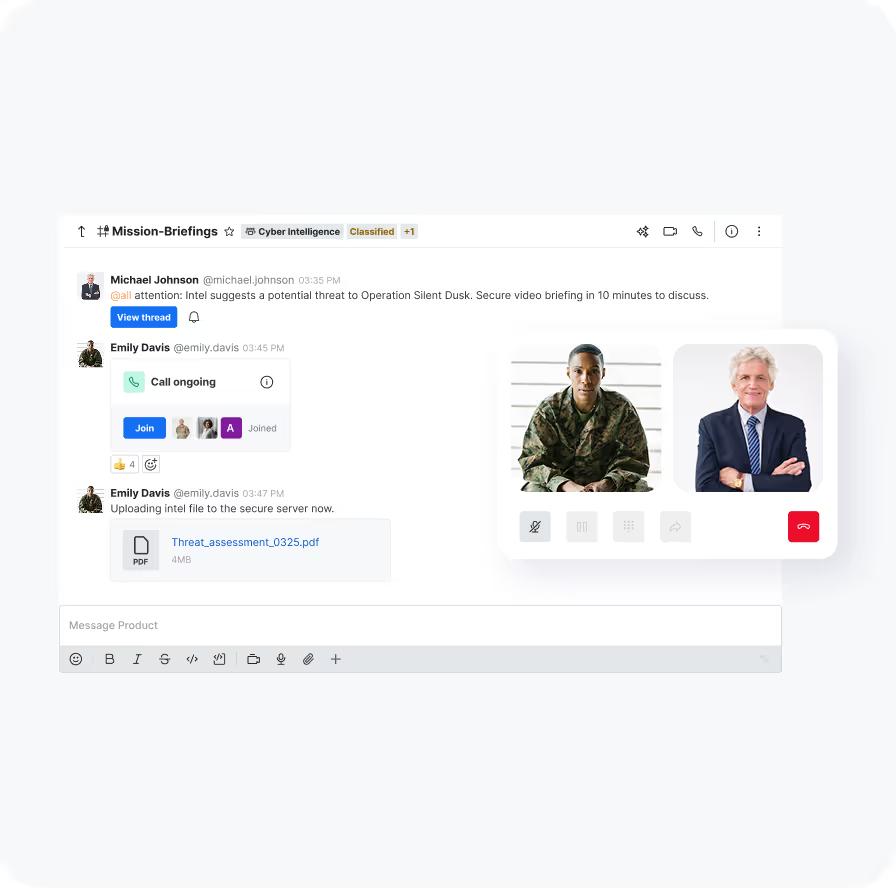
Enable secure, isolated channels for incident response and contingency communication
Enforce ABAC, RBAC, and MFA to control access dynamically and prevent unauthorized entry
Maintain mission-critical uptime through high-availability and COOP-ready deployments
Actively collaborating with leading federal systems integrators, defense contractors, and public sector partners.
Procure via GSA, SEWP, GWACs, and other government-wide vehicles
Align with existing IDIQs, BPAs, and agency-specific frameworks
Awardable through USAF Platform One and Tradewinds Marketplaces
Get expert guidance on pricing, teaming, and subcontracting options

Here’s what our customers and partners have to say


• The insights and data points across this page are informed by the following key sources: Federal CIO Council & DHS: "State of Federal IT"
report (2023), Gartner: Shadow IT impacts on enterprise security (2022), GAO: Interagency communication breakdowns and response delays
(2021), OMB: Federal incident response times and breach likelihood analysis (2022)