Open source software powers nearly everything we build today.
According to the 2024 State of the Software Supply Chain report, open source adoption continues to accelerate.
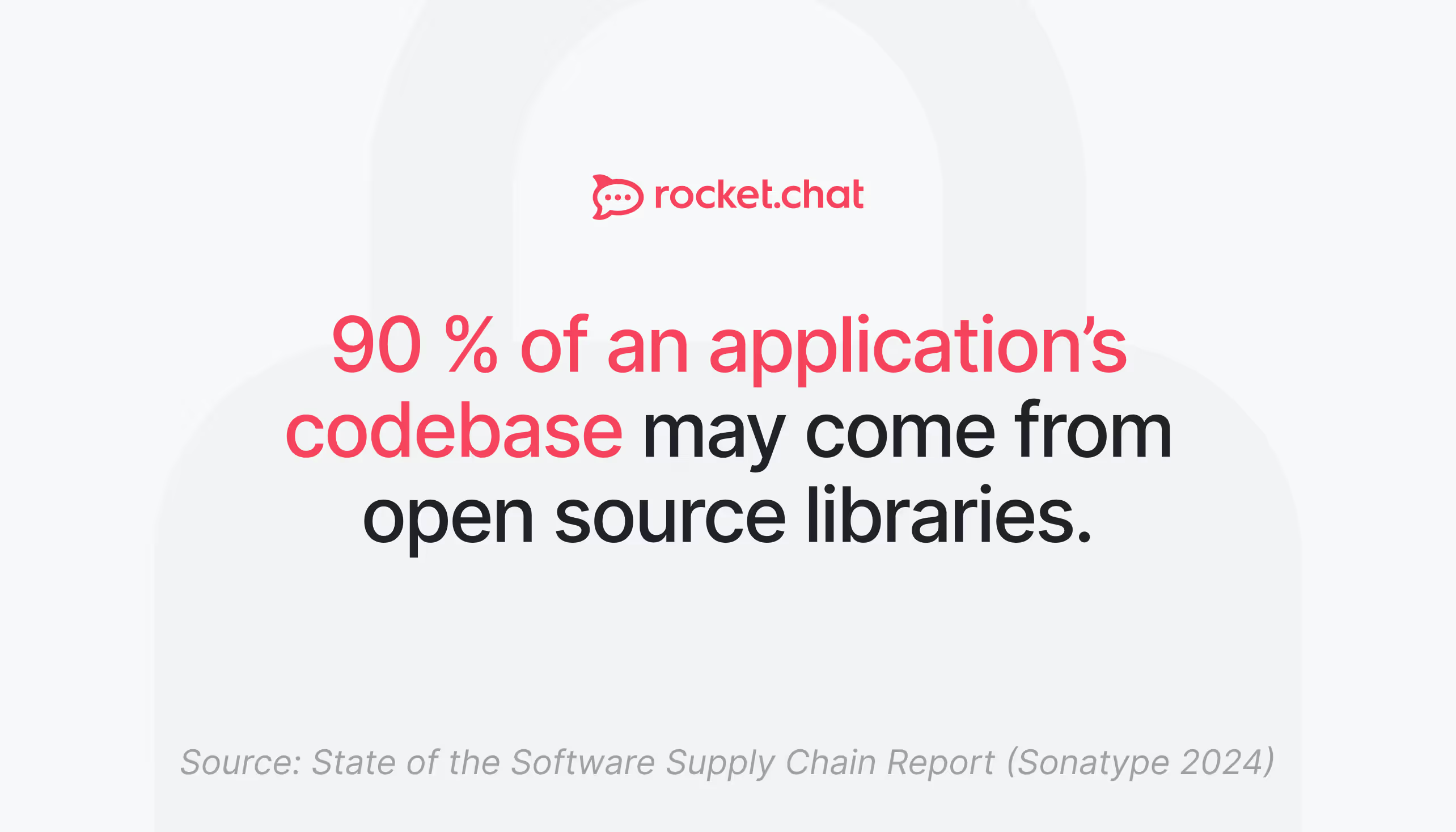
This scale lets teams move fast, share knowledge, and build on proven foundations instead of starting from scratch.
But it also expands the attack surface. The same openness that accelerates innovation can also invite risk.
When a single open source dependency is compromised, its impact can cascade across thousands of applications in a matter of hours.
The recent npm attack made that painfully clear.
When trusted code turns risky
In late September, a few widely used npm packages were compromised in what’s now known as the npm “debug” and “chalk” incident. Attackers injected malicious code into certain package versions, which, when installed, could exfiltrate system information and environment variables.
The good news is that the attack was discovered quickly. The npm security team, along with community researchers, acted fast to remove the affected versions from distribution. Still, the incident was a sharp reminder that software supply chains are now a prime target.
How Rocket.Chat responded
As soon as the incident was reported, our security team conducted a thorough review of all npm dependencies used in Rocket.Chat.
Here’s what we found:
- We only use non-affected versions of a couple of the impacted packages.
- None of the malicious versions identified by Aikido were part of our codebase or supporting services.
- There was no direct risk to Rocket.Chat or our users.
We also recognize and appreciate npm’s swift response in removing the malicious versions from circulation.
Inside our supply chain discipline
Our resilience against incidents like this is a result of deliberate practices that guide how we manage third-party code.

Here are four practices we apply consistently:
1. Full visibility
Every component that goes into Rocket.Chat is tracked through a Software Bill of Materials (SBOM). This gives us a live map of what’s in our stack, where it came from, and who owns it. You can’t secure what you can’t see.
2. Continuous scanning
Automated tools monitor dependencies for known vulnerabilities. Alerts trigger as soon as advisories are published, so we can patch before risk escalates.
3. Verification before adoption
Not every update is a safe update. Before introducing a new dependency or version, we verify its integrity, provenance, and maintainer reputation. This step helps catch tampering attempts early.
4. Layered defense and least privilege
We assume any dependency could one day be compromised. That’s why we isolate environments, apply least-privilege permissions, and enforce code signing where possible to minimize blast radius.
Why supply chain security matters
Software supply chain risk comes from the code you don’t write.
Every modern app relies on hundreds of open source and third-party components.
A single dependency may have hundreds of its own dependencies, each maintained by different people in different parts of the world.
That’s why supply chain risk isn’t just a developer concern, but a boardroom one.

You can’t protect what you don’t know you’re using, and you can’t trust what you can’t verify.
If you’re a security-conscious organization, vulnerabilities in third-party code can mean breaches, data exposure, downtime, and compliance fallout.
At Rocket.Chat, we take that responsibility seriously. Our commitment is not only to build secure software but also to maintain a transparent and verifiable security posture across everything we depend on.
Visibility creates trust
Security isn’t just about defense. It’s about proof.
We know that trust is built when organizations can see, verify, and understand how security is managed.
To make that easier, we’ve launched our Trust Center, a centralized view of Rocket.Chat’s security and compliance posture. It brings together our policies, certifications, and monitoring practices in one transparent space, helping organizations quickly understand how we protect their data.
Because trust isn’t just about having strong controls. It’s also about being able to show them.
A shared path forward
The npm attack won’t be the last supply chain incident. But it can serve as a turning point for how teams think about open source responsibility.
Security doesn’t have to slow innovation. It needs to move in step with it.
As the open source ecosystem grows more interconnected, our collective resilience will depend on small, consistent habits:
- tracking dependencies,
- automating checks, and
- being transparent about the measures we take.
At Rocket.Chat, we’ll continue to build with that mindset: open by design, secure by practice, and transparent by choice.
Frequently asked questions about <anything>


- Digital sovereignty
- Federation capabilities
- Scalable and white-labeled


- Highly scalable and secure
- Full patient conversation history
- HIPAA-ready

for mission-critical operations
- On-premise and air-gapped ready
- Full control over sensitive data
- Secure cross-agency collaboration
%201.svg)

- Open source code
- Highly secure and scalable
- Unmatched flexibility


- End-to-end encryption
- Cloud or on-prem deployment
- Supports compliance with HIPAA, GDPR, FINRA, and more


- Supports compliance with HIPAA, GDPR, FINRA, and more
- Highly secure and flexible
- On-prem or cloud deployment



.png)