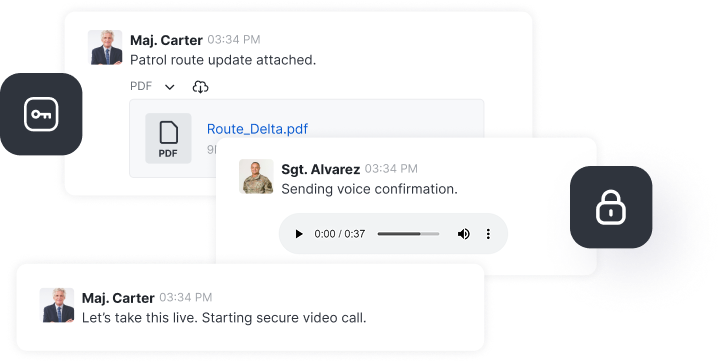
7.13 is a quiet release on the surface but a heavy one under the hood. It is the kind of release that makes everything feel more secure even before you notice what changed.
→ We hardened encryption, sharpened call workflows, tightened governance for federated comms, and set the groundwork for post-quantum security.
If you care about clarity, control, or cryptographic durability, this is the version you will want to update to.
A stronger, more resilient end-to-end encryption foundation
For organizations operating in classified environments, encryption is not optional.
Rocket.Chat has always treated end-to-end encryption as core infrastructure, and in v7.13 we are strengthening that foundation with a series of hardening upgrades that:
- modernize key handling,
- increase resistance to offline attacks,
- improve message integrity, and
- prepare the platform for post-quantum standards.
These enhancements are not new switches or toggles. They are structural upgrades to the underlying cryptography that secure conversations in field operations, intelligence workstreams, interagency missions, and coalition environments.
Here is what we strengthened and why it matters.
Raising the cryptographic baseline
Rocket.Chat is deployed in environments where encryption must hold up under scrutiny.
In this release, we strengthened core components within the key generation and password derivation process. This slows down attackers who try to guess or brute force keys by running massive password-cracking operations offline.
- Key generation is the process that turns a user’s secret passphrase into the cryptographic keys that protect their messages.
- Password derivation is the step that repeatedly transforms that passphrase using a controlled amount of computational work.
In this release, we:
- increased the size of the wordlist used for generating passphrases. A larger wordlist = more possible combinations.
- increased the length of those passphrases. Longer phrases = more entropy
- raised the number of iterations used in the derivation process. More iterations force an attacker’s system to do significantly more work per guess.
Together, these upgrades make key material far more resistant to brute force attempts.
This matters in environments where threat actors may have access to advanced computing resources. By raising the cost of an offline attack, we strengthen confidentiality even against well-resourced adversaries.
Stronger authentication of encrypted messages
Encrypted messages now benefit from stronger integrity protection. We moved from older cipher modes to authenticated encryption, which protects both the confidentiality and the authenticity of each message.
In practical terms, this prevents adversaries from altering or injecting messages even if they manage to intercept the encrypted traffic. This is critical for mission spaces that require high confidence in message authenticity.
Standardized behavior across web and mobile
Encryption must work the same way, regardless of the device.
We improved the consistency in how keys and passwords are generated and managed across web and mobile clients. This reduces inconsistencies, makes audits easier, and ensures users maintain a uniform security posture.
For organizations that rely on mixed-device deployments, this upgrade ensures predictable encryption behavior during field mobility and headquarters operations.
Foundational work for post-quantum encryption
The hardening work in 7.13 aligns directly with our post-quantum roadmap.
Defense and national security programs are already preparing for a world where quantum computation changes the threat landscape.
By tightening cryptographic practices and removing legacy patterns, we can introduce quantum-resistant algorithms in the future without disrupting operations. This lays the groundwork for secure, long-term protection of mission-critical communications.
In conclusion
These improvements require no user action but have a direct impact on mission assurance.
Rocket.Chat continues to treat secure communications as a discipline, not a checkbox. With this release, we take another step toward being the Secure CommsOS that classified programs rely on every day.
Upgrades that strengthen your operational clarity and control
This release brings a set of upgrades that sharpen operational awareness during voice communication. These improvements may look small on paper, but together they reduce friction, increase certainty, and give teams the level of clarity expected in high-stakes environments.
Call context that never gets lost
Every completed, missed, failed, or transferred voice call now auto-generates a clear summary block directly inside the conversation. Analysts, operators, and supervisors no longer have to comb through logs to piece events together. The full call trail stays where your work happens.
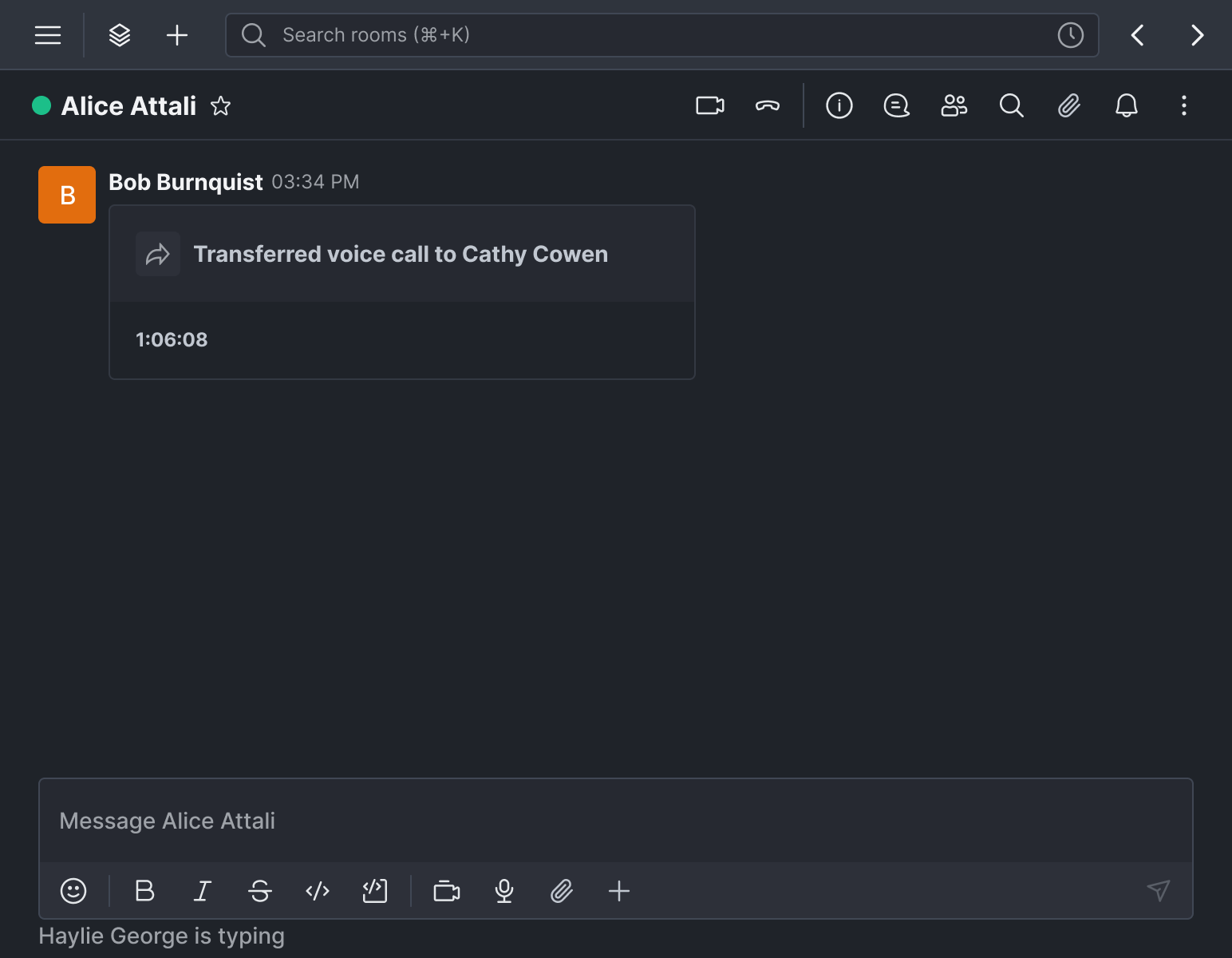
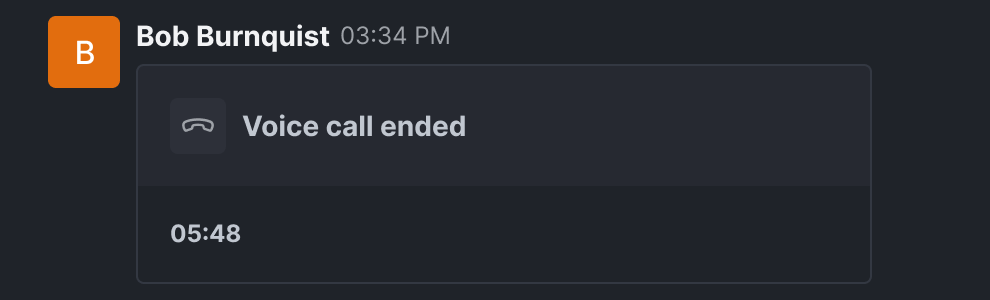
Real-time visibility into mute and hold states
Mute and hold states are now synchronized for both participants during voice calls. When you pause or silence your line, the other party sees it instantly. This removes the confusion that often occurs in voice calls and helps maintain a shared operational picture during critical calls.
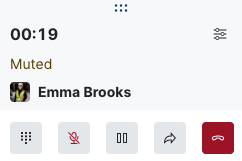
User presence insight before calling or transferring
The call and transfer widgets of a voice call now display the live presence of the selected user inside the call widget. You can avoid calling offline users and can make faster, more informed decisions about routing conversations.
Notification control for busy environments
Users can enable or disable desktop notifications for incoming voice calls. This gives operational teams the ability to manage noise while staying reachable across systems.
Stronger governance for federated communications
A new access-federation permission allows admins to control who can create or join federated rooms. Unauthorized cross-organization communication is blocked, users attempting restricted actions receive clear permission alerts, and admins gain tighter governance over external communications.
Bug fixes
This release includes a number of fixes to improve overall stability, performance, and user experience. For a complete list of resolved issues in Rocket.Chat v7.13, check out the official release notes.
How to update your workspace to the latest Rocket.Chat version?
SaaS workspaces
The release happens automatically on our cloud, so no further action is required from your side. However, remember that updating instances might take a few weeks, so don't hesitate to contact our support team if you need to update your version sooner.
Self-managed workspaces
Depending on the installation mode, you might need to update your server manually. Check out the documentation for instructions.
Frequently asked questions about <anything>


- Digital sovereignty
- Federation capabilities
- Scalable and white-labeled


- Highly scalable and secure
- Full patient conversation history
- HIPAA-ready

for mission-critical operations
- On-premise and air-gapped ready
- Full control over sensitive data
- Secure cross-agency collaboration
%201.svg)

- Open source code
- Highly secure and scalable
- Unmatched flexibility


- End-to-end encryption
- Cloud or on-prem deployment
- Supports compliance with HIPAA, GDPR, FINRA, and more


- Supports compliance with HIPAA, GDPR, FINRA, and more
- Highly secure and flexible
- On-prem or cloud deployment



.png)