
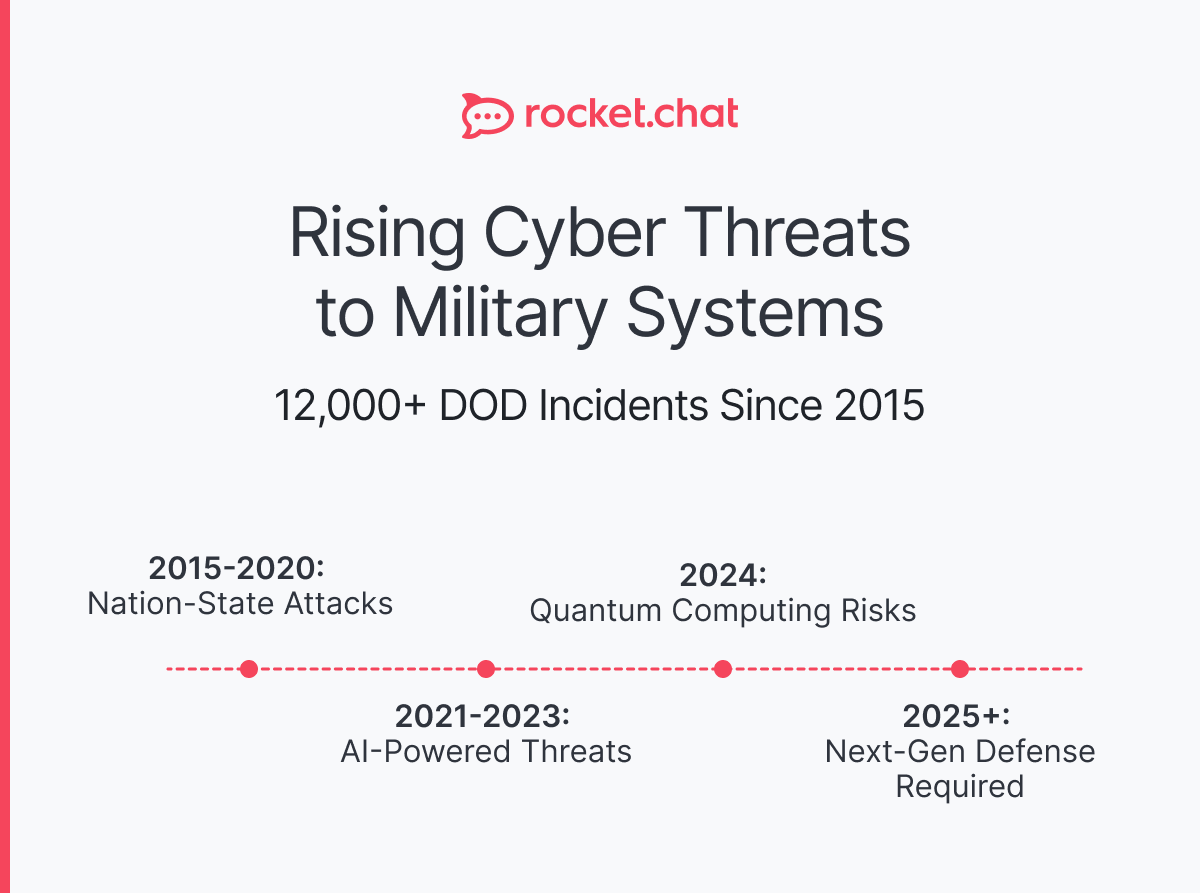
Military communication systems face unprecedented cyber threats, with the U.S. Department of Defense reporting over 12,000 cyber incidents since 2015. This comprehensive guide explores ten critical cybersecurity strategies that protect military communication infrastructure, including end-to-end encryption, real-time threat detection, secure authentication, and advanced malware prevention.
The global military cybersecurity market is projected to grow from $19.2 billion in 2024 to $66.3 billion by 2034, reflecting the escalating importance of secure communications in modern warfare. Learn how military organizations implement NATO-standard protocols, AI-powered security systems, and zero-trust architectures to maintain operational integrity against sophisticated nation-state actors and cyber warfare tactics.
Since 2015, the U.S. Department of Defense (DOD) has reported over 12,000 cyber incidents affecting its systems. This alarming statistic underscores the pressing need for proactive and comprehensive security measures in military communication systems.
Modern warfare relies heavily on advanced communication technologies, which often make these systems prime targets for increasingly sophisticated cyber threats, including ransomware, data theft and espionage, nation-state actors, and Man-in-the-Middle (MitM) attacks.
According to the 2024 Armis Cyberwarfare Report, nation-state actors are actively employing AI-powered tactics for advanced cyber capabilities. This report emphasizes that organizations worldwide are facing unprecedented threat levels.
The global military cybersecurity market demonstrates the critical importance of these systems. Research indicates the market will expand from $19.2 billion in 2024 to $66.3 billion by 2034, growing at a compound annual growth rate (CAGR) of 13.2%. This growth reflects the escalating sophistication of cyber threats and the vital need for robust defense communication systems.
In this context, this article explores the top 10 ways cybersecurity strengthens military communication systems, ensuring secure and efficient operations in an increasingly hostile digital landscape.
Understanding military communication security challenges
Current threat landscape
The 2023 Annual Threat Assessment by the U.S. Intelligence Community highlights that China is almost certainly capable of launching cyberattacks that could disrupt critical infrastructure services within the United States.
In August 2023, Chinese hackers targeted a U.S. military procurement system and several Taiwan-based organizations to exfiltrate data and establish covert proxy networks within the targeted systems.
Market growth and investment
The defense cybersecurity sector is experiencing remarkable expansion. According to RAND Corporation research on military communication systems, effective command and control lie at the heart of any successful military operation. The integration of advanced security solutions into military operations has become non-negotiable.
Key market insights include:
- North America commands 46.1% of the market, driven by strong defense budgets and advanced cybersecurity policies
- Highly sensitive attacks on military systems surged by more than 250% in recent years, forcing defense organizations to boost investment in advanced security controls
- The emphasis on protecting sensitive information from espionage and cyberattacks has led to increased investment in security technologies

Ten cybersecurity strategies that bolster military communication
To prevent devastating breaches and maintain operational superiority, military organizations implement expert-recommended strategies that help maintain robust military messaging and communication channels.
1. End-to-end encryption for secure communication
End-to-end encryption ensures that messages and data shared across military communication networks remain confidential throughout their journey. It protects sensitive military operations from adversaries, guaranteeing that mission-critical information is accessible only to authorized personnel.
Military encryption standards, including AES-256 and NATO-standard algorithms, make intercepted transmissions useless without decryption keys. These protocols are updated continuously to counter evolving cyber threats.
Example: During the 2021 SolarWinds cyberattack, unencrypted data transmissions in government systems were exploited, affecting multiple U.S. federal agencies, including the Pentagon. Implementing robust encryption protocols could have mitigated such vulnerabilities.
2. Real-time threat detection and mitigation
The implementation of real-time threat detection systems powered by AI helps military networks identify and neutralize cyber threats as they emerge. This ensures communication remains intact during operations, reducing downtime and the risk of adversaries exploiting vulnerabilities.
Modern systems incorporate software-defined radios to offer flexibility in the field and allow real-time reconfiguration to counter electronic warfare threats.
Example: In November 2024, the U.S. Army Cyber Command initiated a 12-month pilot of an AI-driven monitoring tool designed to provide scalable, continuous security oversight. The system monitors networks and platforms for threats while analyzing data to find and deter attacks.
3. Secure authentication and access control
Restricting access to secure team chat systems through authentication protocols is fundamental to cybersecurity. Measures such as multi-factor authentication (MFA) and role-based access control (RBAC) ensure that only authorized personnel can access sensitive systems, reducing the risk of breaches.
According to the Cybersecurity and Infrastructure Security Agency (CISA), enabling MFA makes users 99% less likely to be hacked. Additionally, studies have shown that organizations implementing RBAC experience a 50% reduction in security incidents.

4. Protection against data breaches
The 2023 RTF Global Ransomware Incident Map notes that ransomware attacks on government facilities increased significantly in 2023. These attacks pose a serious problem for federal systems, with global incidents rising by 73%.
Cybersecurity measures such as advanced encrypted messaging, secure storage protocols, and data tokenization help protect sensitive military information from falling into enemy hands.
At the 2023 NATO Summit in Vilnius, member states prioritized strengthening their cyber defenses, especially for critical infrastructure. They launched the Virtual Cyber Incident Support Capability (VCISC), which provides rapid support and resources to enhance members' cyber resilience.
5. Safeguarding against jamming and interference
Communication jamming is a common tactic used by adversaries to disrupt mission-critical communications by interfering with radio frequencies.
To tackle this, military systems deploy:
- Frequency Hopping Spread Spectrum (FHSS) for rapid frequency switching
- Encrypted frequencies that resist interception
- Low Probability of Intercept/Detection (LPI/LPD) waveforms for covert operations
- Anti-jamming technologies that ensure clear communication in hostile environments
These technologies ensure operational continuity even when adversaries attempt to disrupt communication security.
6. Cyber resilience through redundancy
Designing systems with multiple, diverse pathways for mission-critical functions decreases the likelihood that a single attack can disrupt all communication channels simultaneously. Research indicates this approach ensures that if one path is compromised, alternative routes maintain operational continuity.
Implementing backup systems, secure failovers, and redundant communication channels enables operations to continue seamlessly. This represents a core principle of out-of-band communication strategies.
The 2023 DOD Cyber Strategy underscores the need for comprehensive cyber resiliency and hardening of electronic systems to address current and future cyber threats.
7. Preventing insider threats
Insider threats, whether from rogue employees or compromised personnel, pose a significant risk to secure communication systems. Monitoring tools and behavioral analytics detect unusual activity patterns and prevent malicious insiders from causing harm through enhanced organizational security.
Example: Following Edward Snowden's leaks in 2013, agencies like the NSA implemented numerous technical measures to control data access and enhance oversight. The National Insider Threat Task Force (NITTF) was established to help agencies develop effective insider threat programs.
8. Advanced malware detection and prevention
AI-driven solutions proactively identify and block malicious software, such as ransomware and spyware, before they can compromise military communication networks. These systems are tailored to detect sophisticated threats targeting high-value military systems, providing an extra layer of protection comparable to the most secure messaging apps.
Example: The U.S. military currently utilizes the Panoptic Junction (PJ) tool, developed by Army Cyber Command, for continuous monitoring and detection of anomalous behavior on military networks.
9. Ensuring secure interoperability
Military operations often involve government communication between allied forces and different branches of service. Cybersecurity frameworks ensure that such interoperability is seamless while maintaining data security.
Key frameworks include:
- NATO Cyber Defence Policy for alliance-wide standards
- Risk Management Framework (RMF) for systematic security assessment
- Security Technical Implementation Guides (STIGs) for technical compliance
- NIST Cybersecurity Framework for comprehensive risk management
- MIL-STD-2045 secure communication protocols
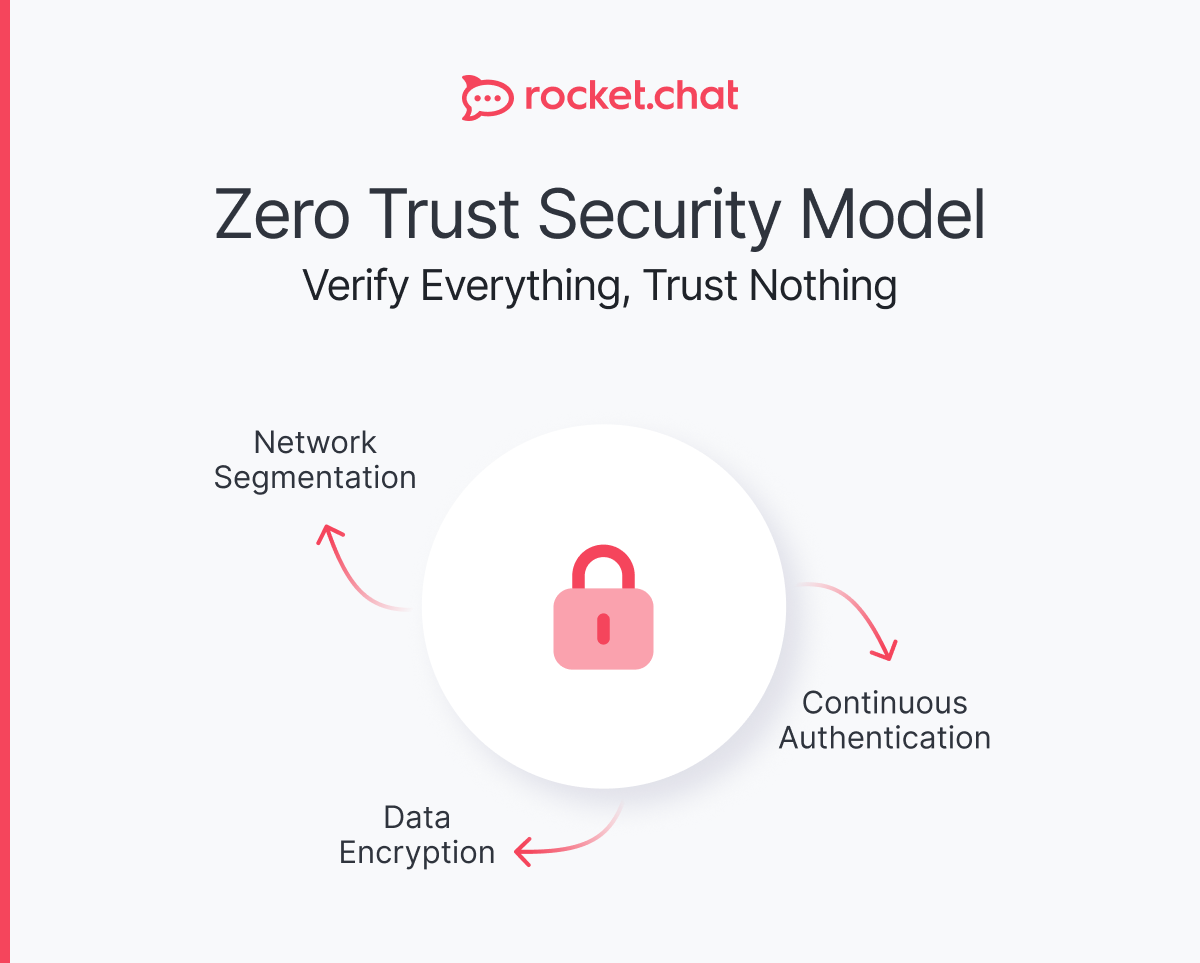
- Zero Trust model assuming verification for every access attempt
These frameworks enable coordinated efforts across chat platforms and instant messaging platforms without exposing sensitive data to breaches.
10. Compliance with international cybersecurity standards
Adherence to international standards like NATO's cybersecurity framework and ISO 27001 ensures that military systems maintain robust protocols for communication security. Compliance not only improves internal operations but also builds trust among international allies.
This standardization paves the way for seamless collaboration across government chat systems and government messaging apps, enabling effective workplace team communication in multinational operations.
Comparison of military cybersecurity approaches
How Rocket.Chat enhances military communication
Used by privacy-focused organizations in sectors such as government, education, healthcare, and defense, Rocket.Chat is an open-source secure communication platform that addresses the unique challenges of military operations.
Comprehensive security features
Rocket.Chat provides a chat app solution with comprehensive capabilities:
- End-to-end encryption: All communications benefit from robust encryption, ensuring that sensitive military data remains protected from interception by adversaries
- Secure collaboration tools: Personnel can share information effectively through secure team chats and military chat features
- Real-time threat detection: Integration with advanced monitoring systems detects and mitigates security threats in real time
- Customizable open-source framework: Military organizations can customize the platform to meet specific security and operational needs
- Flexible deployment: Options include on-premises, cloud, or air-gapped collaboration for maximum security
Operational advantages
The platform supports seamless integration with existing communication tools and systems, ensuring secure interoperability across allied forces and different military branches. This makes it ideal for organizations requiring both sophisticated security and practical usability.
The future of military communication security
The integration of emerging technologies continues to shape next-generation security systems:
- Artificial intelligence-driven monitoring to detect and counter intrusions automatically
- Quantum-resistant encryption to protect against future computational threats
- Advanced satellite communications for resilient long-range coordination
- Software-defined networking for adaptive security responses
- Blockchain-based authentication for immutable access records
According to research, the military cybersecurity market will continue expanding as geopolitical tensions increase, artificial intelligence integration advances, and the need for secure communication grows in military operations.
Summary
Military communication systems form the backbone of modern warfare, and their security remains a top priority. From end-to-end encryption to real-time threat detection, these cybersecurity measures ensure the confidentiality, integrity, and availability of critical communication channels.
The global military cybersecurity market's projected growth to $66.3 billion by 2034 reflects the escalating importance of these systems. Organizations that implement comprehensive security strategies, comply with international standards, and leverage advanced technologies position themselves to maintain operational superiority in an increasingly contested cyber domain.
To implement these measures quickly and without technical hassle, Rocket.Chat offers cutting-edge features like end-to-end encryption, flexible deployment options, secure team chats, and interoperability to meet the unique demands of military operations.
Contact Rocket.Chat today to learn how our platform can enhance your military communication security.
Frequently asked questions about military communication
What is military communication and why is cybersecurity critical for it?
Military communication refers to the systems and protocols used to transmit sensitive operational, tactical, and strategic information between military units, commanders, and allied forces. Cybersecurity is critical because modern military operations rely heavily on digital communication networks that are prime targets for nation-state actors, cyber terrorists, and sophisticated adversaries. With the U.S. Department of Defense reporting over 12,000 cyber incidents since 2015, robust cybersecurity measures protect classified data, maintain operational continuity, and prevent adversaries from intercepting or disrupting mission-critical communications. The global military cybersecurity market growing to $66.3 billion by 2034 demonstrates the escalating importance of securing these vital systems.
How does end-to-end encryption protect military communications?
End-to-end encryption protects military communications by ensuring that data remains encrypted throughout its entire transmission journey, from sender to recipient. This means that even if adversaries intercept the transmission, they cannot decode the information without the proper decryption keys. Military-grade encryption uses advanced algorithms like AES-256 and NATO-standard protocols that are continuously updated to counter evolving cyber threats. This technology proved essential following the 2021 SolarWinds attack, where unencrypted government communications were exploited. By implementing end-to-end encryption, military organizations ensure that sensitive operational data, tactical plans, and classified intelligence remain confidential and accessible only to authorized personnel with proper authentication.
What role does AI play in military communication security?
Artificial intelligence plays a transformative role in military communication security through real-time threat detection, automated response systems, and predictive analysis. AI-powered tools continuously monitor network traffic, identify anomalous behavior patterns, and neutralize cyber threats before they compromise communication systems. The U.S. Army Cyber Command's 12-month pilot of the Panoptic Junction AI-driven monitoring tool exemplifies this capability, providing scalable security oversight across military networks. AI systems analyze vast amounts of data to detect sophisticated attacks, including advanced persistent threats and zero-day exploits. Additionally, AI enhances malware detection by learning attack patterns and adapting defenses accordingly, making military communication networks more resilient against evolving cyber warfare tactics employed by nation-state actors.
How do military organizations ensure secure communication with allied forces?
Military organizations ensure secure communication with allied forces through standardized cybersecurity frameworks, interoperable encryption protocols, and compliance with international standards. NATO's Cyber Defence Policy, Security Technical Implementation Guides (STIGs), and the NIST Cybersecurity Framework provide common security baselines that enable seamless cooperation while maintaining data protection. Secure communication protocols like MIL-STD-2045 facilitate coordinated operations without exposing sensitive information. The Zero Trust model, which requires strict verification for every user and device, ensures that even multinational operations maintain robust security. Organizations also implement suite-based encryption systems that allow different nations' forces to communicate securely while respecting individual sovereignty requirements and compliance regulations.
What are the biggest cyber threats facing military communication systems today?
Military communication systems face multiple sophisticated cyber threats, including ransomware attacks that increased 73% globally in 2023, nation-state actors conducting cyber espionage and data exfiltration, Man-in-the-Middle (MitM) attacks intercepting communications, communication jamming disrupting radio frequencies, and insider threats from compromised or malicious personnel. The 2024 Armis Cyberwarfare Report highlights that nation-state actors employ AI-powered tactics for advanced cyber capabilities, while the 2023 U.S. Intelligence Community Threat Assessment notes that China is capable of launching cyberattacks to disrupt critical infrastructure. Additionally, attacks on military systems surged by over 250% in recent years, with sophisticated adversaries targeting command and control systems, satellite communications, and cryptographic equipment to gain strategic advantages.
How does Rocket.Chat support military communication requirements?
Rocket.Chat supports military communication requirements through its comprehensive security features designed specifically for defense operations. The platform provides end-to-end encryption for all communications, ensuring sensitive military data remains protected from adversary interception. Its flexible deployment options allow organizations to choose on-premises, cloud, or air-gapped installations based on security needs and compliance requirements. Rocket.Chat's open-source framework enables military organizations to customize the platform for specific operational demands while maintaining full control over their communication infrastructure. The system integrates seamlessly with existing military communication tools, supports real-time threat detection, and complies with international security standards including NATO protocols. Used by privacy-focused government and defense organizations worldwide, Rocket.Chat delivers secure team collaboration without compromising operational security.
What is the Zero Trust security model in military communications?
The Zero Trust security model in military communications is a cybersecurity approach that assumes no user, device, or network should be automatically trusted, regardless of whether they are inside or outside the organization's network perimeter. This model requires strict identity verification for every person and device attempting to access resources, continuously validates security posture, and implements least-privilege access principles. In military contexts, Zero Trust is essential because threats can originate from both external adversaries and internal sources. The model employs multiple layers of defense including multi-factor authentication, micro-segmentation of networks, continuous monitoring of user behavior, and real-time risk assessment. By implementing Zero Trust architecture, military organizations protect against advanced persistent threats, prevent lateral movement by attackers, and ensure that even if one system is compromised, adversaries cannot easily access other critical communication systems.
How do frequency-hopping systems protect against jamming attacks?
Frequency-hopping systems protect against jamming attacks by rapidly switching communication channels across multiple frequencies in a predetermined sequence known only to authorized parties. This Frequency Hopping Spread Spectrum (FHSS) technology makes it extremely difficult for adversaries to jam communications because they would need to simultaneously jam all possible frequencies, which requires significantly more power and resources. Military radios employ advanced frequency-hopping algorithms that change frequencies hundreds or thousands of times per second, combined with spread spectrum techniques that distribute signals across wide frequency bands. When integrated with Low Probability of Intercept/Detection (LPI/LPD) waveforms and encrypted frequencies, these systems ensure communication continuity even in hostile electronic warfare environments where adversaries actively attempt to disrupt military operations through radio frequency interference.
What compliance standards govern military cybersecurity?
Military cybersecurity is governed by multiple compliance standards that ensure robust security protocols and interoperability. Key frameworks include NATO's Cybersecurity Framework and Cyber Defence Policy for alliance-wide coordination, the NIST Cybersecurity Framework (particularly important for U.S. military systems), ISO 27001 for information security management, Security Technical Implementation Guides (STIGs) for technical configuration standards, the Risk Management Framework (RMF) for systematic security assessment, MIL-STD-2045 for secure communication protocols, and FIPS 140-2/140-3 for cryptographic module validation. The 2023 DOD Cyber Strategy emphasizes comprehensive cyber resiliency requirements, while NATO's Security Manual for Licensed Defence Industries (SMLDI 2025) expands requirements for data management and vendor compliance. Organizations must also comply with COMSEC (Communications Security) standards and undergo regular government-vetted security reviews.
What is the difference between defensive and offensive military cybersecurity?
Defensive military cybersecurity focuses on protecting military communication systems, networks, and data from cyber threats through measures like firewalls, intrusion detection systems, encryption, access controls, and continuous monitoring. These capabilities prevent unauthorized access, detect anomalies, and respond to security incidents to maintain operational integrity. Offensive military cybersecurity, conversely, involves active operations to disrupt, degrade, or destroy adversary capabilities through cyber means, including penetrating enemy networks, conducting cyber reconnaissance, deploying malware against hostile systems, and executing electronic warfare operations. While defensive cybersecurity in 2024 represents a significant portion of military spending (with the market valued at $19.2 billion), both capabilities are essential for maintaining cyber superiority. Modern military doctrine increasingly recognizes that effective cybersecurity requires both robust defensive measures to protect critical infrastructure and offensive capabilities to deter adversaries and achieve strategic objectives in cyberspace.
Frequently asked questions about <anything>


- Digital sovereignty
- Federation capabilities
- Scalable and white-labeled


- Highly scalable and secure
- Full patient conversation history
- HIPAA-ready

for mission-critical operations
- On-premise and air-gapped ready
- Full control over sensitive data
- Secure cross-agency collaboration
%201.svg)

- Open source code
- Highly secure and scalable
- Unmatched flexibility


- End-to-end encryption
- Cloud or on-prem deployment
- Supports compliance with HIPAA, GDPR, FINRA, and more


- Supports compliance with HIPAA, GDPR, FINRA, and more
- Highly secure and flexible
- On-prem or cloud deployment


.avif)


