
This comprehensive guide explores encrypted messaging and its critical role in protecting your digital privacy. Learn how end-to-end encryption works, why major platforms like WhatsApp and Signal use it, and how to choose the right secure messaging app for your needs. Discover the latest statistics showing that over 2 billion people now use encrypted messaging daily, understand the difference between encryption types, and get practical tips for maximizing your communication security. Whether you're concerned about privacy, business security, or simply want to understand modern encryption technology, this guide covers everything you need to know.
Your private conversations deserve to stay private. Every day, billions of messages travel across the internet, and without proper encryption, these communications are vulnerable to interception, surveillance, and data breaches. Encrypted messaging has evolved from a niche security feature into an essential tool for anyone who values their digital privacy.
In an era where cyber attacks have increased by 38% year-over-year and data breaches expose millions of personal records annually, understanding how to protect your communications isn't just smart—it's necessary. Choosing from the growing number of secure chat platforms available today requires understanding the fundamentals of encryption and your specific security needs. This guide will walk you through everything you need to know about encrypted messaging, from basic concepts to choosing the right platform for your needs.
What is encrypted messaging?
Encrypted messaging is a method of communication that uses cryptographic protocols to scramble your messages so only the intended recipient can read them. Think of it as sending a letter in a locked box that only the person with the correct key can open.
When you send an encrypted message, the content is transformed into unreadable code using complex mathematical algorithms. Even if someone intercepts the message during transmission, they'll see nothing but meaningless gibberish without the decryption key.
The evolution of secure communication
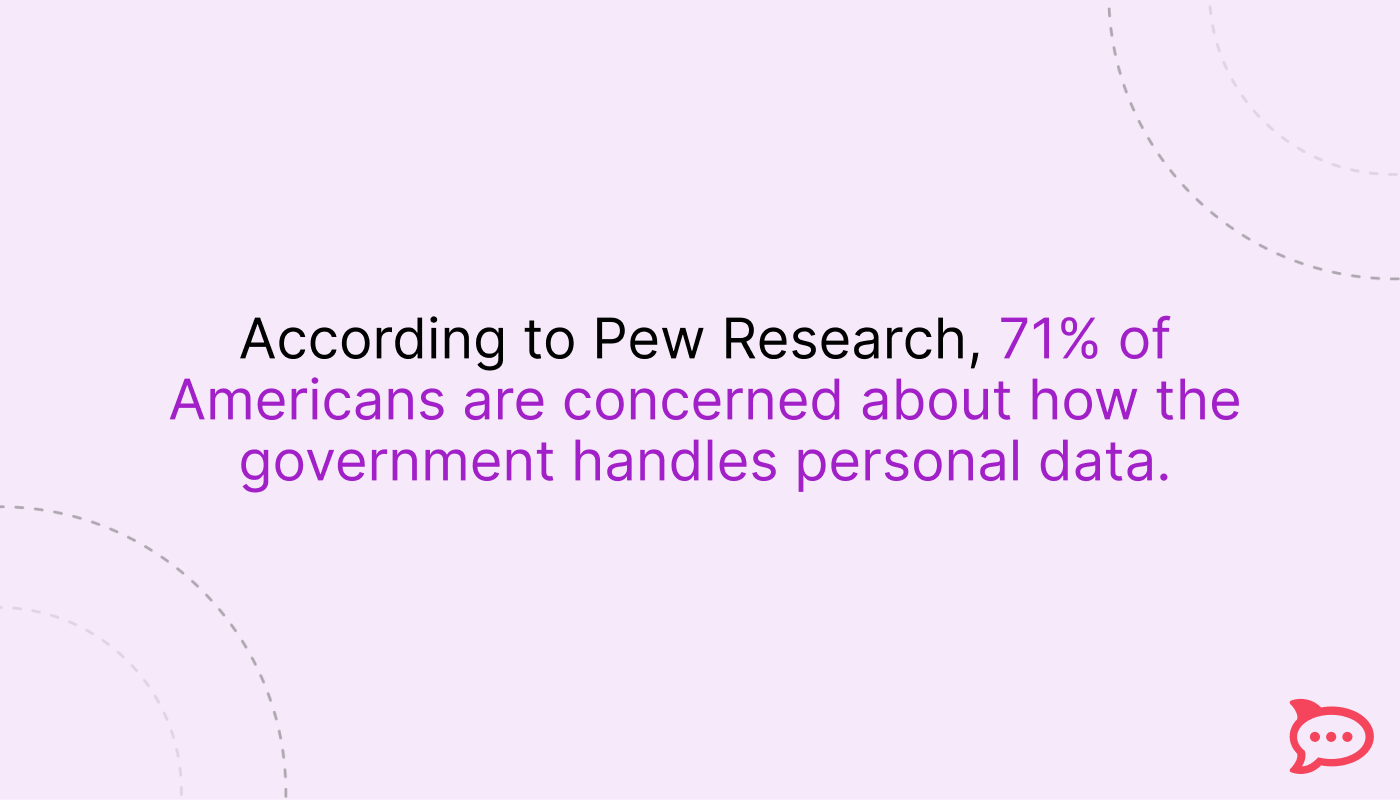
Digital encryption isn't new, but its widespread adoption in messaging apps is relatively recent. According to research from the Pew Research Center, 71% of Americans now say they're concerned about how companies use their data. This growing awareness has pushed messaging platforms to prioritize security features.
The shift toward encrypted messaging accelerated dramatically after 2013, when revelations about mass surveillance programs highlighted the vulnerability of traditional digital communications. Today, end-to-end encryption has become the gold standard for privacy-conscious users and organizations alike.
How does end-to-end encryption work?
End-to-end encryption (E2EE) represents the highest level of messaging security. With E2EE, messages are encrypted on your device before they're sent and can only be decrypted by the recipient's device. Not even the messaging service provider can access the content.
The technical process simplified
Here's what happens when you send an end-to-end encrypted message:
Key generation: When you install an encrypted messaging app, it generates a unique pair of cryptographic keys—a public key and a private key. Your public key can be shared with anyone, while your private key stays securely on your device.
Message encryption: When you hit send, the app uses the recipient's public key to encrypt your message. This transforms readable text into encrypted data that looks like random characters.
Secure transmission: The encrypted message travels through the internet and the service provider's servers, but remains unreadable throughout the journey.
Decryption: When the message reaches the recipient, their device uses their private key to decrypt it back into readable text. Only their private key can unlock messages encrypted with their public key.
This process happens instantly and automatically, requiring no technical knowledge from users. The Stanford Internet Observatory notes that modern encryption protocols can secure messages in milliseconds while maintaining user-friendly interfaces.
Types of encryption in messaging apps
Not all encrypted messaging is created equal. Understanding the differences helps you choose the right level of security for your needs.

End-to-end encryption
This is the most secure option. Messages remain encrypted from the moment they leave your device until they reach the recipient. Popular apps using true E2EE include Signal, WhatsApp, and iMessage (for iPhone-to-iPhone messages).
Transport layer encryption
Also called encryption in transit, this method encrypts messages between your device and the service provider's servers, and again between the servers and the recipient. However, the service provider can technically access your messages while they're stored on their servers. Many standard SMS text messages and some messaging apps use only this level of encryption.
Client-side encryption
Similar to E2EE but with some variations in implementation. The encryption happens on your device (client-side) rather than on external servers, giving you more control over your data.
Why encrypted messaging matters
The importance of encrypted messaging extends far beyond protecting casual conversations. Here's why it's become essential in modern digital life.
Protecting personal privacy
Your messages contain sensitive information about your life, relationships, and activities. Research from the Electronic Frontier Foundation shows that messaging data can reveal detailed patterns about your behavior, location, and social connections, even when the content itself seems mundane.
Without encryption, this data is vulnerable to various threats including hackers, malicious insiders at service providers, and unauthorized surveillance. Encrypted messaging ensures your private conversations remain truly private.
Business and professional security
Companies face even higher stakes. According to IBM's Cost of a Data Breach Report, the average cost of a data breach reached $4.45 million in 2023. Encrypted messaging protects confidential business communications, trade secrets, and client information from corporate espionage and data theft.
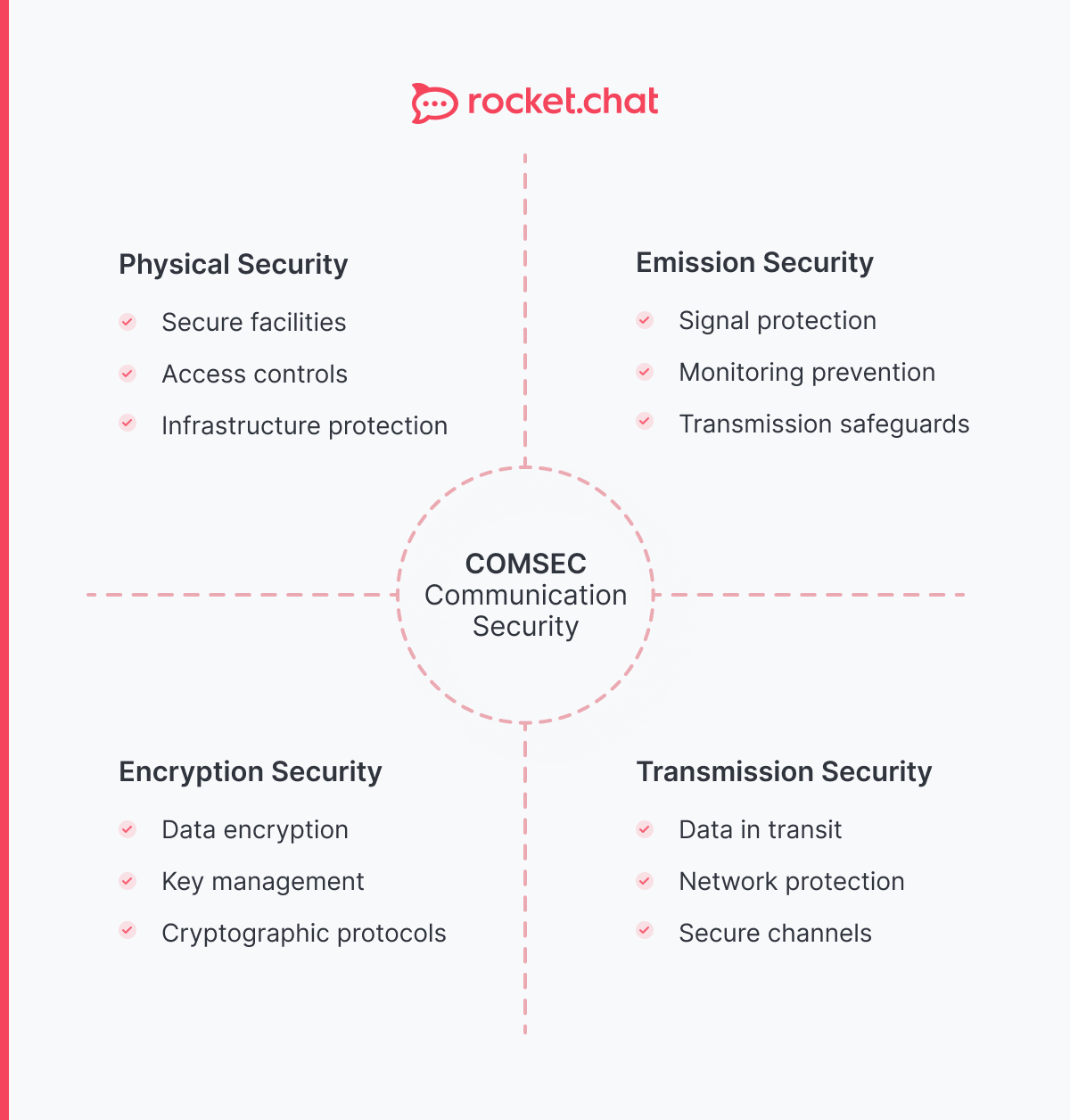
Many industries with strict compliance requirements—including healthcare, finance, and legal services—now mandate encrypted communications to meet regulatory standards like HIPAA, GDPR, and financial data protection laws.
Journalist and activist protection
For journalists, whistleblowers, and human rights activists, encrypted messaging can be literally life-saving. It enables secure communication with sources, protects sensitive information from authoritarian governments, and allows activists to organize safely.
Preventing identity theft and fraud
Unencrypted messages can be intercepted and used for identity theft, financial fraud, or social engineering attacks. Encrypted messaging adds a crucial layer of protection against these threats.
Popular encrypted messaging apps compared
Choosing the right encrypted messaging app depends on your specific needs, technical comfort level, and who you need to communicate with. While consumer apps like Signal and WhatsApp dominate the personal messaging space, organizations should evaluate options that meet their specific security and compliance requirements. For a deeper dive into platform options, explore our comprehensive guide to encrypted messaging apps for organizations.
Signal
Often considered the gold standard for privacy, Signal offers true end-to-end encryption for all communications. The app collects minimal metadata and is open-source, allowing security experts to verify its claims. Signal supports text, voice, video calls, and group messaging.
Best for: Privacy purists, journalists, activists, and anyone prioritizing security above all else.
With over 2 billion users worldwide, WhatsApp combines strong end-to-end encryption with mainstream accessibility. Owned by Meta, it uses the Signal Protocol for encryption but collects more metadata than Signal.
Best for: General users who want security without sacrificing a large user base and familiar features.
iMessage
Apple's messaging service provides automatic end-to-end encryption for conversations between Apple devices. Messages are seamlessly integrated into the iOS ecosystem, but encryption doesn't extend to SMS conversations with Android users.
Best for: Apple users communicating primarily with other iPhone owners.
Telegram
Telegram offers optional end-to-end encryption through "Secret Chats" but doesn't encrypt standard messages end-to-end by default. It's known for large group chat capabilities and custom features.
Best for: Users who want flexibility and advanced features, understanding the security trade-offs.
Key features to look for in encrypted messaging apps
When evaluating encrypted messaging platforms, consider these essential features. Whether you're comparing consumer apps or enterprise solutions, understanding what makes the most secure messaging apps stand out helps you make informed decisions.
Verified end-to-end encryption
Don't just take the app's word for it. Look for apps that use well-established, audited encryption protocols like the Signal Protocol. Open-source applications allow independent security researchers to verify encryption claims.
Minimal data collection
Even with encrypted messages, apps can collect metadata about who you talk to, when, and how often. Choose apps with transparent, minimal data collection policies.
Self-destructing messages
Some apps offer disappearing messages that automatically delete after a set time. This feature adds an extra layer of privacy by ensuring sensitive conversations don't remain accessible indefinitely.
Security indicators
Quality apps provide visual confirmation that conversations are encrypted, often through lock icons or color-coded indicators. Some also offer safety numbers or verification codes that let you confirm you're communicating with the intended person.
Cross-platform availability
Your encrypted messaging app should work across all your devices—smartphones, tablets, and computers—while maintaining security on each platform.
Common encrypted messaging myths debunked
Several misconceptions about encrypted messaging persist. Let's clarify the facts.
Myth: Only criminals need encryption
Reality: Everyone benefits from encryption. Just as you lock your doors and close your curtains, encrypting your digital communications is a basic privacy precaution. Legitimate users include businesses protecting trade secrets, healthcare providers securing patient information, and ordinary people maintaining their right to privacy.
Myth: Encryption makes you a surveillance target
Reality: Encrypted messaging has become so mainstream that using it raises no red flags. Billions of people use WhatsApp, iMessage, and other encrypted platforms daily for completely ordinary conversations.
Myth: Law enforcement opposes all encryption
Reality: While debates continue, many law enforcement agencies acknowledge encryption's importance for cybersecurity. The discussion centers on balancing security with investigative needs, not eliminating encryption entirely.
Myth: Encrypted apps are difficult to use
Reality: Modern encrypted messaging apps are just as user-friendly as unencrypted alternatives. The encryption happens automatically in the background, requiring no technical knowledge from users.
Setting up encrypted messaging: step-by-step guide
Getting started with encrypted messaging is simpler than you might think.
Step 1: Choose your app
Based on your needs and the people you communicate with most, select an encrypted messaging app. For maximum privacy, Signal is hard to beat. For mainstream compatibility, WhatsApp offers solid security with a massive user base.
Step 2: Download and verify
Download your chosen app from official sources only—the Apple App Store, Google Play Store, or the app's official website. Avoid third-party app stores that might distribute compromised versions.
Step 3: Create your account
Most encrypted messaging apps require only a phone number for registration. Some allow additional security measures like PIN codes or biometric authentication.
Step 4: Enable all security features
Once installed, explore the app's settings and enable all available security features including screen security, disappearing messages (if desired), and app locks.
Step 5: Verify contacts
Many encrypted apps offer contact verification through safety numbers or QR codes. While optional, this step confirms you're communicating with the intended person and not an imposter.
Step 6: Educate your contacts
Encourage the people you communicate with regularly to switch to encrypted messaging. Security improves when both parties use encrypted platforms.
Best practices for secure messaging
Even with strong encryption, following security best practices maximizes your protection. Implementing comprehensive communication security protocols ensures your encrypted messaging strategy addresses all potential vulnerabilities.
Keep your app updated
Install updates promptly. They often include critical security patches that protect against newly discovered vulnerabilities.
Use strong device security
Your encrypted messages are only as secure as your device. Enable strong passwords or biometric locks, encrypt your device storage, and be cautious about installing unknown apps.
Be careful with backups
Some encrypted messaging apps offer cloud backups for convenience, but these backups may not be encrypted with the same strength as your messages. Understand your backup options and choose security over convenience when necessary.
Avoid screenshots
Screenshots of sensitive conversations can undermine encryption. The images aren't encrypted and could be inadvertently shared or backed up to cloud services.
Think before clicking links
Phishing attacks remain effective even in encrypted messages. Verify unexpected links before clicking, especially if they request login credentials or personal information.
Specialized encrypted messaging use cases
Beyond personal and standard business communications, certain sectors require enhanced security measures tailored to their unique operational requirements.
Government and defense communications
Government agencies and defense organizations face sophisticated threats that demand the highest levels of security. Government communication systems must meet stringent security standards while enabling efficient inter-agency collaboration. Similarly, defense communication systems require encryption protocols that can withstand nation-state level threats.

Military operations specifically benefit from military communication platforms designed for tactical environments. These systems often incorporate features like out-of-band communication capabilities for redundancy when primary networks fail. For sensitive military operations, military messaging solutions and military chat systems provide secure coordination across units.
Air-gapped and high-security environments
Organizations handling classified information often operate in air-gapped environments—networks physically isolated from the internet. Air-gapped collaboration tools enable secure team communication without internet connectivity, crucial for intelligence agencies and critical infrastructure operators. Government messaging apps designed for these environments provide the security needed while maintaining usability for government personnel.
Framework compliance
Organizations must often demonstrate compliance with established security frameworks. The NIST cybersecurity framework provides guidelines that inform secure messaging implementations, particularly for government contractors and regulated industries. Choosing platforms that align with these frameworks simplifies compliance while strengthening security posture.
Encrypted messaging for businesses
Organizations face unique communication security challenges that encrypted messaging helps address.
Compliance requirements
Many industries must comply with regulations requiring encrypted communications. Healthcare organizations must protect patient information under HIPAA, while financial institutions must secure client data per various financial regulations. Understanding organizational security frameworks and requirements helps businesses choose messaging platforms that meet their compliance obligations.
Preventing corporate espionage
Business communications contain valuable intellectual property, strategic plans, and confidential client information. Encrypted messaging platforms designed for enterprises offer security features tailored to organizational needs, including message retention policies and administrative controls. Organizations looking to implement secure team chat solutions need platforms that balance usability with enterprise-grade security.
Remote work security
With distributed teams becoming the norm, employees communicate sensitive information from various locations and networks. Encrypted messaging provides consistent security regardless of where team members work. For organizations in high-stakes industries, implementing mission-critical communications systems with built-in encryption becomes essential for operational continuity.

Solutions for organizations
Enterprise-focused encrypted messaging platforms like Wickr, Wire, and Signal for Business offer additional features including centralized management, compliance tools, and integration with existing business systems. Effective workplace team communication requires platforms that scale with your organization while maintaining security standards. Organizations evaluating options should consider both instant messaging platforms and comprehensive chat app solutions that integrate with existing workflows.
The future of encrypted messaging
Encryption technology continues to evolve, with several emerging trends shaping the future.
Post-quantum cryptography
Current encryption relies on mathematical problems that would take conventional computers thousands of years to solve. However, quantum computers could theoretically break these encryption methods. Researchers are developing quantum-resistant encryption algorithms to future-proof communications against this potential threat.
Decentralized messaging protocols
New approaches aim to eliminate central servers entirely, distributing message routing across networks of users. This makes surveillance or service shutdowns much more difficult.
Integration with other privacy tools
Expect to see encrypted messaging increasingly integrated with VPNs, secure email, and encrypted cloud storage, creating comprehensive privacy ecosystems. Modern secure collaboration tools are evolving to provide unified platforms that address multiple security needs simultaneously, from messaging to file sharing to video conferencing.
Regulatory developments
Ongoing debates about encryption policy will shape what's legally permissible. Stay informed about legislation in your jurisdiction that might affect encrypted messaging availability or requirements.
Troubleshooting common encrypted messaging issues
Even secure platforms occasionally present challenges. Here are solutions to frequent problems.
Messages not delivering
If messages won't send, first check your internet connection. Then verify the recipient has the same app installed and updated. Restarting the app often resolves temporary glitches.
Cannot verify contact
If you're unable to verify a contact's safety number, ensure both parties are using the latest app version. The verification process may fail across different versions.
App consuming too much data
Encrypted messaging uses slightly more data than unencrypted alternatives due to encryption overhead. In settings, look for options to reduce data usage, like lowering media quality for mobile data connections.
Group messages not working
Group messaging sometimes fails if one member uses an outdated app version or has blocked certain participants. Ensure all group members are running current versions.
Making the switch to encrypted messaging
Transitioning from unencrypted to encrypted messaging requires some planning but delivers significant security benefits.
Communicate the change
Let your contacts know you're switching to encrypted messaging and explain the benefits. Many people will follow your lead once they understand the privacy advantages.
Migrate gradually
You don't need to switch all communications at once. Start with your most sensitive conversations and gradually expand as contacts adopt encrypted apps.
Handle the holdouts
Some contacts may resist changing apps. For these relationships, you might maintain multiple messaging apps temporarily while encouraging adoption of secure alternatives.
Export important conversations
If you're switching between encrypted platforms, check whether you can export conversation histories. Note that exports may not maintain the same encryption level.
Conclusion
Encrypted messaging has transformed from a specialized security tool into an essential privacy protection for everyday digital communication. Whether you're protecting personal conversations, securing business communications, or defending sensitive information, end-to-end encryption provides the foundation for truly private digital dialogue.
The good news is that using encrypted messaging no longer requires technical expertise or sacrifice of convenience. Modern platforms combine robust security with user-friendly interfaces, making privacy accessible to everyone.
By understanding how encryption works, choosing the right platform for your needs, and following security best practices, you take control of your digital privacy. In a world where data breaches and surveillance grow increasingly common, encrypted messaging isn't paranoid—it's prudent.
Start today by selecting an encrypted messaging app, installing it, and encouraging your regular contacts to make the switch. Your future self will thank you for protecting your private communications now.
Frequently asked questions about <anything>
encrypted messaging
What is the most secure encrypted messaging app?
Can encrypted messages be hacked?
Is WhatsApp really end-to-end encrypted?
Do encrypted messaging apps work without internet?


- Digital sovereignty
- Federation capabilities
- Scalable and white-labeled


- Highly scalable and secure
- Full patient conversation history
- HIPAA-ready

for mission-critical operations
- On-premise and air-gapped ready
- Full control over sensitive data
- Secure cross-agency collaboration
%201.svg)

- Open source code
- Highly secure and scalable
- Unmatched flexibility


- End-to-end encryption
- Cloud or on-prem deployment
- Supports compliance with HIPAA, GDPR, FINRA, and more


- Supports compliance with HIPAA, GDPR, FINRA, and more
- Highly secure and flexible
- On-prem or cloud deployment


.avif)


